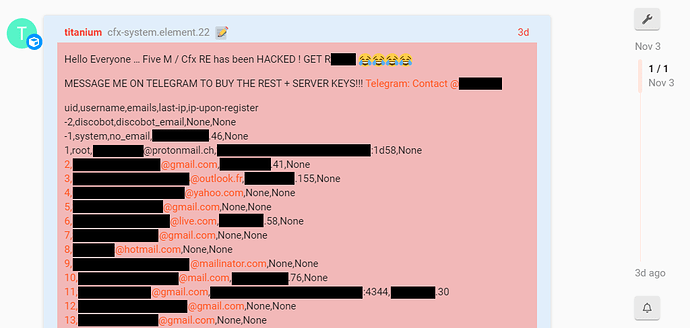
On November 3rd, 2022, we discovered a malicious actor had illegally gained access to an unused account with moderator access. Using this account, the attacker was able to extract a limited amount of account information from registered users on our forums. In our commitment to transparency, security and your privacy we’re sharing the details leading up to this incident.
What data was retrieved
It is regrettable someone was able to access an unused moderator account to scrape account data off our forums. This scraping was performed by using the forum API which the moderator account had access to. Fortunately this API doesn’t expose much, only a limited amount of account data was accessible to the attacker.
This means that no passwords could be retrieved and your account is safe. Your uploaded assets, Patreon perks and upvotes were not accessible to the attacker and are not compromised.
The attacker was however able to to acquire server license keys through Keymaster’s internal management portal which the compromised account had access to, and limited account data accessible through Discourse’s moderator panel. In summary, the following information was exposed to the attacker:
- Forum account information:
- Username;
- Email address;
- IP address, limited to your IP at account sign-up, and the IP you last logged in with
- Server license keys
Since server license keys were exposed to the attacker, we will be taking measures against reuse. All server keys will be regenerated to prevent misuse and we’ll be notifying all server owners when this happens. More on that below.
Notes:
- None of the accounts you have linked with Cfx.re (Steam, Discord, etc.) were exposed.
- A server license key is purely for server-list registration purposes and can not give any other party access to the actual server’s databases and/or any other of its files.
- Discourse is the name of our forum software.
How the incident happened
As you may know, many members of the FiveM team have been using element names from the periodic table as their pseudonyms. Back in 2016, we wrote a script to programmatically create forum users for each element from the periodic table. This allowed us to post messages as different element names through a forum plugin we developed. Each of these element accounts were assigned a random unknown password, never to be directly logged in to, and only to be used through our forum plugin.
We stopped using those element accounts on the forums in 2019, and left them for what they were. They had a random password that no one knew, so no one would be able to log in to them. Or so we thought.
On November 3rd, one of those element accounts suddenly popped up. The attacker used a compromised element account to create a post in which they revealed to have access to account data.
This obviously raised alarm bells and we immediately began investigating. We soon discovered that on October 12th the attacker was able to access multiple of those element accounts. They did this by brute-forcing passwords using a large amount of IP addresses to mask their attempts.
Starting October 17th up until November 3rd, the attacker was able to scrape account data off our forums. This happened at a rate that was unnoticeable by our metrics. Once we discovered the post created by the attacker, we disabled all element accounts to prevent further use.
What we realized is that when those element accounts were created, the randomly generated passwords were not up to modern standards. This made the passwords insecure and easier to brute-force. Furthermore, 2-factor authentication (2FA) was never enabled on these accounts as they were not used like normal accounts, they were used through a forum plugin to create posts under the element pseudonyms. All other moderators and administrators on our forum are required to have 2FA enabled; their accounts are safe.
On October 22nd we noticed suspicious activity in some of our internal logs, but was mistaken at the time for artifacts that came from another internal system that was using the same Application Programming Interface (API) and therefore not acted upon.
What actions were taken
We have taken the past 3 days to extensively assess the situation and take measures to prevent this from happening in the future.
- We’ve identified the entry point and the full scope of the data breach;
- We’ve disabled all of the afore-mentioned element accounts and removed their permissions;
- We’ve audited our logs to confirm nothing else has been compromised;
- We’ve released an initial change to Keymaster to prepare for the upcoming license key regeneration.
What server owners should do
We strongly recommend server owners to regenerate their active license keys on Keymaster.
To do so, log in on https://keymaster.fivem.net/ and click on the ID of your server. Next, click on the ‘Regenerate’ button next to the key details (as shown below). Repeat this for each of your servers.
Then update your server configuration with the newly generated key.
Non-regenerated license keys will automatically be regenerated
An automated regeneration of all server license keys will take place on Monday, November 14th, 2022. License keys won’t be regenerated again if you generated or regenerated them after November 3rd.
Note: If someone else uses your license key for their server, they will only be able to confuse our server lists’ backend. The server list might then alternate between displaying your and their server.
What we’re doing next
- We are in the process of notifying all relevant Data Protection Authorities (DPAs) of the breach.
- Server license keys will be regenerated by November 14th. A notification will be sent out to all relevant server owners.
- Keymaster will encode license keys in our database to prevent them from being read by anyone but the server owner.
- We’re changing internal security & audit policies to prevent breaches like these from happening again.
It pains us that this has happened, wishing we were able to act sooner to prevent the incident, as we care for your personal data and your ability to safely enjoy the platform! We’re putting in all the necessary work to prevent this from happening again.