– to a mod; if you think this should go elsewhere please feel free to move it ![]()
Hello forum peoples! This is my first topic here, following this I’ll be releasing quite a few custom resources to help give back to the community.
I’m making this post to inform you all in a more serious manner than done previously, an exploit that allows your entire server to be kicked, temporarily banned, turned into whales, and plenty of other things.
This is all based around FiveM’s NUI system, and it’s some pretty serious stuff if you’re not watching what you’re downloading and slapping into your server. If you inspect some of your addons, you’ll notice functions labeled ‘RegisterNuiCallback’ – these can be used to to send messages back to the client from NUI based menu’s; it works great when it’s being used the right way.
Unfortunately, it doesn’t take a whole lot of creativity to exploit these functions; especially when the server doesn’t check the information the client is sending to it.
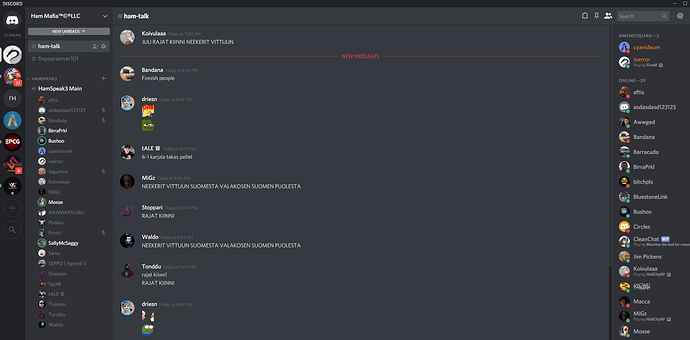
This is our popup discord; we went around to every server with this vulnerability and kicked the entire server with a message displaying our discord, which had channels in it explaining how to fix it.
Short form patch? esx_spectate, mellotrainer, esx_k9, and most custom mdt systems are wide open to this exploit. Get rid of them.
Can’t part with your beloved addons? No problem; simply gather some more information about the client and the information they’re sending to the server and then allow the server to make the informed decision on whether or not to actually allow the requested command to be performed.
tl;dr delete esx_spectate, and mellotrainer
I’ll be posting a much bigger topic on this, and a walk-through on how to secure other resources such as your car dealer, garages, banking systems, and home systems against data editing with cheat engine and other programs.
We also owe a few people apologies if they feel they’ve been wronged after our little exploit spree; just give this topic a good read and we hope that you’ll make smarter decisions about the code you run on your servers.
 Otherwise all good points I can agree with. I probably took too much of an attack approach then a different one, based off of a couple of things said in OP. But ayy it’s a discussion forum right
Otherwise all good points I can agree with. I probably took too much of an attack approach then a different one, based off of a couple of things said in OP. But ayy it’s a discussion forum right 

 . It is important that people in the community are exploiting with the intent to better understand the security of this platform and informing others of its flaws so that the developers can either patch these issues, or server owners can implement their own fixes. Posting a big topic entirely based on these ideas including best practices with examples later for the purpose of education, not for the purpose of discussing my own moral compass. I’ll link that here when it’s up.
. It is important that people in the community are exploiting with the intent to better understand the security of this platform and informing others of its flaws so that the developers can either patch these issues, or server owners can implement their own fixes. Posting a big topic entirely based on these ideas including best practices with examples later for the purpose of education, not for the purpose of discussing my own moral compass. I’ll link that here when it’s up.